
The ECLIPSE Authentication System: Integration with Azure AD
24 Aug, 2023
The following article shows the integration of ECLIPSE with Azure Active Directory (Azure AD). Azure AD can be used for your team to access external resources, such as Microsoft 365, and other SaaS applications.
ECLIPSE Software Suite has an agnostic authentication system. It can be flexibly used with other systems and can be coupled with most client Single Sign-On (SSO) solutions. Therefore, it can be used as a system that allows users to authenticate once and access other resources. The benefits of an SSO are clear, higher efficiency and less time wasted. ECLIPSE has a similar concept to Microsoft ADFS SSO.
Default Authentication System
Of course, a default authentication system is provided within ECLIPSE (based on Apereo CAS, providing the same features like Dual Factor Authentication, password policy, etc.). The Default protocol ensures options provided by the Administrator for authentication and allows access control to ECLIPSE.
Integration with Azure AD
This integration is based on SAML (Security Assertion Markup Language), an open standard for exchanging authentication and authorisation data between an identity provider and a service provider. SAML is an XML-based markup language for security assertions, which are statements that service providers use to make access-control decisions.
The SAML specification defines three roles:
- The principal, generally a user
- The identity provider (IdP) => Azure AD
- The service provider (SP) => ECLIPSE
How does the Integration Flow work?
There are several steps needed for the integration with Azure AD. The following diagram shows the Azure AD – ECLIPSE Authentication Flow:
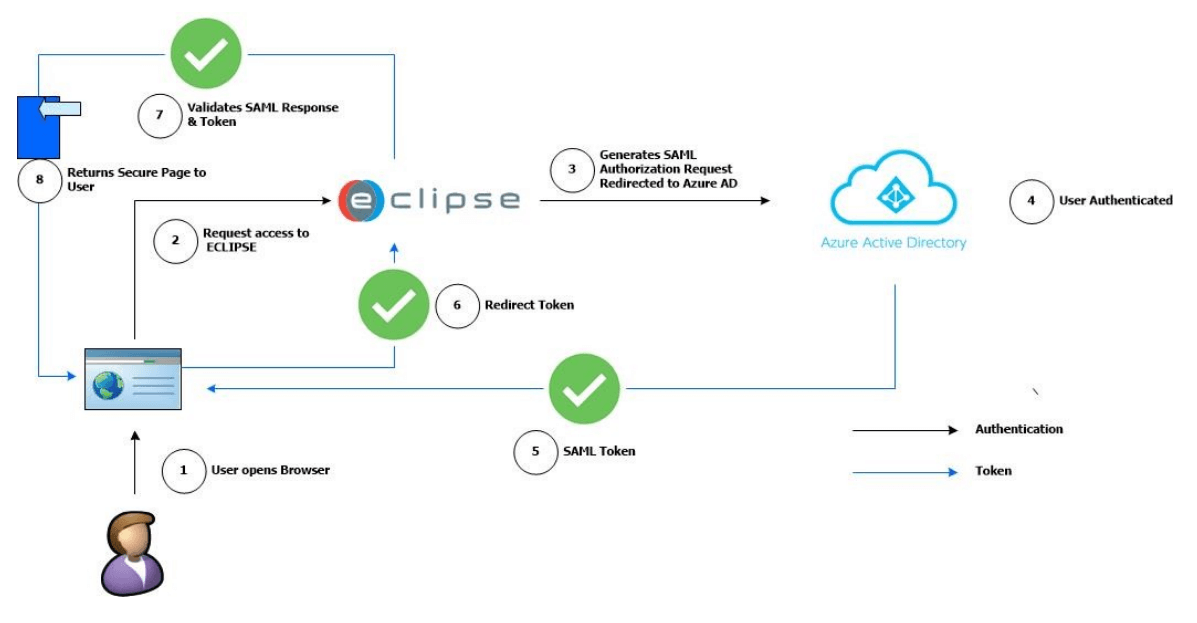
Below you can also find the steps present inside of the diagram.
- User opens browser
- Request access to ECLIPSE
- Generates SAML authorization request redirect to Azure AD
- User Authenticated
- SAML token
- Redirect token
- Validates SAML Response & Token
- Returns secure page to user
Components of the integration system:
The main components in the diagram above are:
- User: The person that accesses ECLIPSE
- Web browser: The component that the user interacts with ECLIPSE
- ECLIPSE: Enterprise application that supports SAML and uses Azure AD as an identity provider (IdP).
- Token: A SAML assertion (also known as SAML tokens) that carries sets of claims made by the IdP about the principal (user). It contains authentication information, attributes, and authorisation decision statements.
- Azure AD: Enterprise cloud IdP that provides SSO and Multi-factor authentication for SAML apps. It synchronises, maintains, and manages identity information for users while providing authentication services to relying applications.
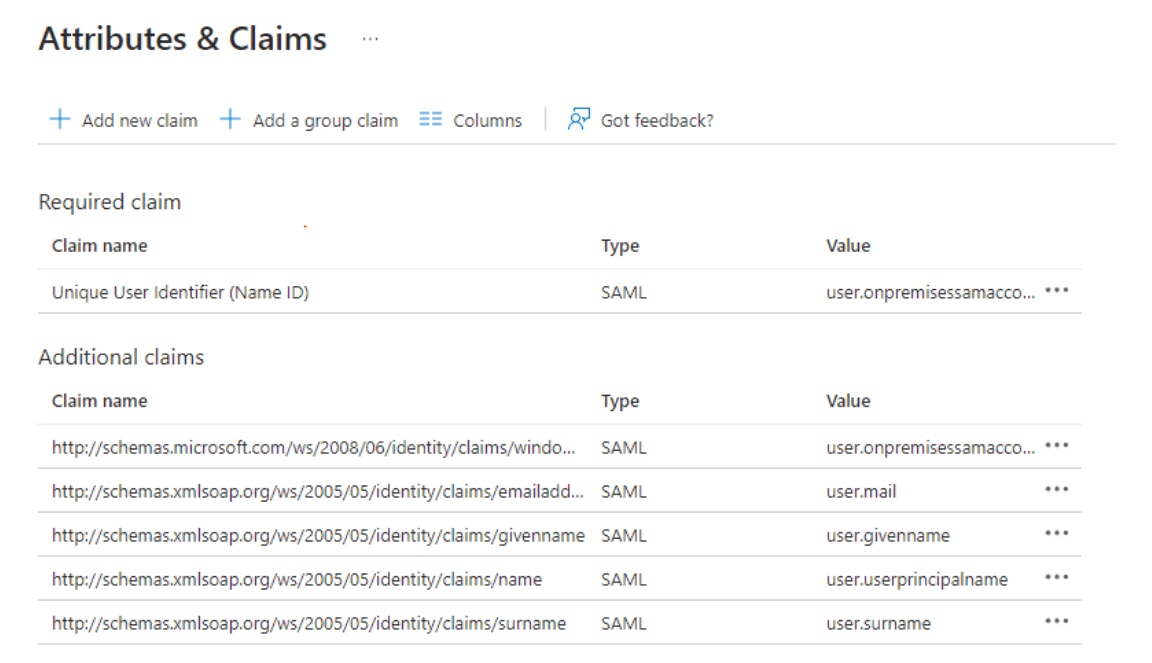
Attributes & Claims in Azure AD Enterprise application
To perform this integration, an Azure AD Enterprise application must be created. The important task is to configure the Attributes & Claims. The returned claim must match the ECLIPSE username (e.g., SAMAccountName => user.onpremisessamaccountname).
Efficiently working with ECLIPSE
We recommend implementing an Azure AD or another SSO so you and your organisation can access ECLIPSE faster and easier. Through the images and text above, we hope you understand the benefits and implementation of this feature. If you have any questions or would like to know more about ECLIPSE, you can easily contact us.
